8 Ways to Stay Safe Online
by Ian Uymatiao
Let’s face it: We all love the Internet. There are so many awesome things we can do on the web that we have a hard time imagining a world without it. The problem, however, is that it can also be quite dangerous. Much like streets, parks, subways and malls, the Internet is a public place; and like most public places, we inadvertently expose ourselves to risks that could have huge consequences.
However, we all still end up going to these public places because we were taught at an early age to be street-smart, to not let these dangers get the better of us. Fortunately, the same can also be said about the Internet. If you are street-smart (or net-smart in this case), you can have strong confidence that nothing bad will happen to you online anytime soon. This article aims to educate (or remind) you on some of the dangers that lurk on the web, and what you can do to easily thwart them.
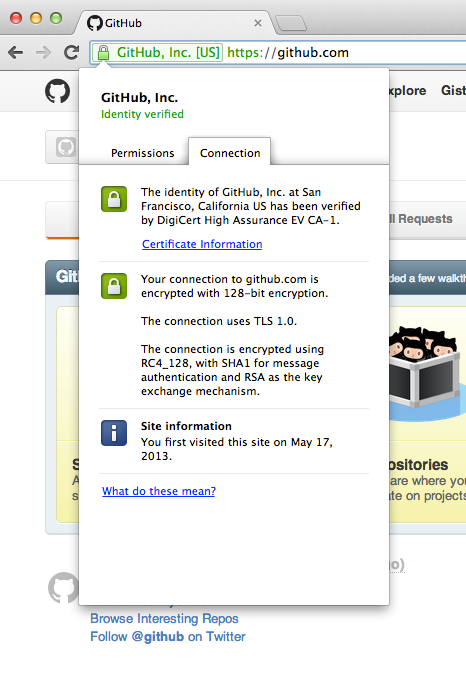
1. Always check for HTTPS during logins
Whenever we transmit or receive data over a network, there is always the risk that somebody will be eavesdropping on the network, seeking juicy information to exploit. If that network happens to be transmitting passwords, sensitive messages, or credit card numbers, you can imagine just how much damage an eavesdropper can cause with that information in hand.
The easiest way to thwart this risk is the use of HTTPS. You are probably already familiar with HTTP being a universal protocol for sending data on the web; HTTPS is simply HTTP with an extra step for security. The gist of what HTTPS does is that the data to be transmitted will first be scrambled in such a way that only the rightful receiver of the data will be able to unscramble it. This process is known as encryption; and it is used to guarantee that only the rightful recipient of the data will be able to read its contents, while eavesdroppers will only be able to derive random gibberish.
In the real world, HTTPS is what makes it safe for us to send sensitive data like passwords over the Internet. Whenever you are about to log in to a site with your account, you must always make sure that the URL shows https instead of the usual http. As long as it’s the former, you can feel safe that your data will not be compromised when you send it. If you want to absolve yourself of the burden of always looking at the URL bar to safe, you can also install HTTPS Everywhere, a plugin for Firefox and Chrome that forces websites to use HTTPS all the time.
The padlock icon shows that all incoming and outgoing web traffic is encrypted
2. Do not use easy-to-guess passwords
It’s easy to see how this can easily damage you. If your password is easy to guess, it’s only a matter of time before a hacker can get into your account and cause havoc. This is especially dangerous when computers are involved, because a hacker can easily set his/her computer to guess your password at alarming rates.
The quickest solution would be to use a password that is difficult (as in really difficult) to guess, even for a beefy machine. There are many guides online that will help you come up with a strong password, but the main rules to follow are that they should be long (at least 12 characters) and should not be obvious nor easy to discern. A couple of techniques include using a whimsically nonsense sentence, and compressing a sentence into a seemingly random password. Get creative!
3. Do not reuse passwords
Using the same password over multiple accounts is an easy way to propagate the damage. If the hacker manages to guess your passwords for one account, your other accounts are pretty much screwed since the hacker instantly got the password for them as well. As a means of damage control, you should always make sure that every account has a unique password.
This, of course, opens up a new problem. We have so many online accounts to juggle, and yet we are supposed to think up a unique and secure password for each and every one of them? Unfortunately, yes, but fortunately, you don’t have to memorize them all. You can use a password manager, an app or service that will memorize your dizzying number of complex passwords so that you don’t have to. It works by asking the user to enter a master-password in order to unlock a database of stored passwords. Think of it like using a key that you always keep with you to unlock a safe that stores all of your other keys. As a bonus, many of these password managers come with the feature of auto-filling in the password whenever you login, saving you the hassle of copying and pasting the passwords every time.
If you are worried about the idea of trusting your passwords to an application or service, know that password managers were built with security and privacy in mind. The database remains strongly encrypted until it is unlocked, and because only you know what the master password is, nobody else (not even the app provider) can find out the contents of the database. In other words, the data inside is truly for your eyes only. There are a handful of free options available, including Lastpass and Dashlane, so check them out, and see which one best suits your needs.
4. Enable two-factor authentication
Sometimes it can’t be helped, and a hacker does manage to bypass the password part of a login process. In this worst case scenario, an age-old proverb comes into mind: never put all your eggs in one basket. In other words, don’t just rely on passwords for keeping the bad guys out. This is the basis for two-factor authentication, which is another way of saying that you need something else other than your password if you want to get in.
Most implementations of two-factor authentication use something known as the one-time code. After the usual password is entered correctly, the user is also asked to enter a generated code before he/she is allowed entry into the account. This code can either be sent to your phone via SMS, or generated offline using an app like Google Authenticator. What makes two-factor authentication work is that the attacker can’t get in unless he/she is also able to correctly enter the one-time code, which is only possible if he/she is also in possession of the phone that is either receiving or generating it. Without both factors (password and one-time code) authenticated, the attacker is shut out of the account.
Because two-factor authentication brings a lot of security with it, everyone is encouraged to turn on two-factor authentication. Right. Now. Many services you know and love already support it, including Gmail, Outlook, Facebook, Dropbox, WordPress, Lastpass, Dashlane, and even Guild Wars 2. There is no reason not to stay one step ahead of a password-cracking hacker.
5. Always check for spoof websites
If an attacker can’t guess your password or one-time code, there is always the option of fooling you into giving it to him/her. This is commonly known as phishing; and it involves fooling users into thinking they are logging into the actual web service, when in fact it is a spoof of the real thing, designed to snatch passwords that users enter. Many phishing attempts come in the form of an email, which is intentionally written and designed in such a way that an untrained eye would think it’s the real thing. If the user takes the bait, the account is pretty much compromised.
There are a couple of ways to sniff out these fake sites and emails. The first way involves checking the origin of the email. If the email is about a Gmail account reset, but the sender’s email address does not even come from a Google domain, you can easily dismiss the email as fake. Another way involves links. For really well-disguised emails, following the link to a fake website could have devastating consequences. An easy way to avoid this situation is to NOT follow the link, but rather enter the URL of the real website yourself. This way, you can be confident in the legitimacy of the website when dealing with sensitive actions such as account resets or password changes.
6. Update your computers
Our operating systems and apps are not perfectly secure; and security holes are being discovered all the time. This means that until they are patched, these holes remain avenues for cyber-attacks. A good rule of thumb is to always update your OS and apps to the latest version, as these patches often involve plugging security holes.
The one exception to this rule is if a patch is found to seriously destabilize the system, usually due to a torrent of new bugs. However, if these patches are deemed harmless, then there is no reason to delay updating your software.
7. Disable plugins such as Java and Flash when they’re not needed
It is often overlooked that plugins are actually a popular venue of attack for hackers. Arguably more so than any other kind of software, browser plugins are plagued with security holes left and right. Just look at the popular Java plugin as an example. Nowadays, the security reputation of the Java plugin is bad. Very, very, very bad. Flash, on the other hand, while not as serious as Java, also has problems of its own.
The problem with browser plugins, unfortunately, is that they are often necessary for a satisfying web experience. Fortunately, very few websites, if any, rely on the use of the Java plugin, but the same cannot be said about Flash. For better or worse, Flash is here to stay if you want to continue enjoying YouTube videos.
The best advice available is that when it comes to plugins, block them by default, and only unblock specific plugin content when it’s needed. This way, no Flash or Java content can run automatically upon loading a page; you are always in control. By selecting which plugin content are allowed to run, you can at least continue to enjoy your YouTube videos while preventing some malicious ActionScript code from wreaking havoc on your computers.
Turning Flash off by default can save bandwidth and battery.
It can also prevent malicious code from running in the background.
8. Backup. Always Backup.
Here’s the thing. Backup will always be important, even outside the context of security. With that said, should an attacker somehow succeed in raising hell on your computer, the first thing you should have is a clean backup of your files. There is no guarantee that the files on your hard drive are in good condition once the attacker has been forced out of your system. On such an occasion, you would want to be able to resume from a recent backup, rather than start from scratch.
If you happen to own a sizable external hard drive, you owe it to yourself to backup your data regularly. If something fatal happens to your data, such as a malware-initiated wipe, you will at least have something to fallback on. As for backup utilities, both Windows Backup for Windows and Time Machine for Mac make it quick and painless for users to get that important backup running. Of course, you don’t have to stop there. Because some security attacks can also compromise the backup drive itself, it would also be a good idea to make an online backup of your data. You can either backup only your most important files to free online storage services like Dropbox, or you can backup your entire digital life to a premium backup service like Crashplan or Backblaze.
Sometimes, despite all the barriers we’ve put up, an online attacker can still get the better of us. If we can’t protect ourselves then, the least we can do is bounce back from the carnage. If you really want to prevent the worst from happening, backup early, and backup often.

Comments